ISO 27701 As an extension to ISO 27001
Processes and communication increasingly take place in digital form, which makes information security so important. Many organisations therefore consider a good management system to be essential in this area.
ISO 27001 provides an excellent basis for this and allows you to demonstrate that your valuable information is suitably protected.
However, recently a new standard was published as an extension to ISO 27001, namely ISO 27701. This standard not only protects your own information, but also shows that you protect the privacy of others.
Defined roles in data protection management
The roles defined in ISO 27701 are Controller (organization responsible for PII – personally identifiable information) and Processor (responsible for PII processing on behalf of another organization). These roles are defined in Article 1 Paragraph (4) and (5) of the Law of the Republic of Indonesia No. 27 of 2022 (PDP Law) and in ISO 29100.
Controller
"Any legal person, public authority, and international organization which, alone or jointly with others, determines the purposes and means of the processing of personal data.”
The controller collects personal data and determines the purposes for which they will be used and the means of the processing. More than one organization can act as PII controller for the same processing, and these are then generally referred to as Joint Controllers. In this case, agreements on data exchange is necessary.
Benefits of the PII Controller role
- The Controller receives guidelines for preferred ways of working
- The role facilitates transparency between PII Controllers
- It also ensures effective management of PII processes
Processor
"Any legal person, public authority, and international organization which, alone or jointly with others, which processes personal data on behalf of the controller".
The Processor processes personal data for the PII Controller, and only works according to the controller’s instructions.
Benefits of the PII Processor role
- Receives guidelines for preferred ways of working
- Provides customers with reassurance that PII is handled effectively
Benefits of ISO 27701 certification
Possession and use of personal data are naturally associated with risk. However, these data are often essential for operation of the business and must therefore be used in accordance with the regulations in order to reduce the risk as far as possible.
If you approach this systematically by using ISO 27701, you are taking active steps to mitigate privacy risks. The measures introduced in your organisation reduce risks and also offer better protection against data leaks.
Organizations which (further) process personal data on behalf of their customers must offer sufficient guarantees that the processing complies with the requirements of the Law of the Republic of Indonesia No. 27 of 2022 about Personal Data Protection(PDP). Through the use of a Personal Information Management System (PIMS) you create documented evidence of how personal data are processed. This demonstrates that you have carefully considered the personal data processing and shows the actions you have taken.
Organizations which fall under the PDP Law can demonstrate with ISO 27701 certification that they have taken suitable technical and organizational measures in order to guarantee fulfilment of the PDP Law (even if the ISO data protection security certificate is not a "PDP Certificate” as such).
An ISO 27701 Certificate shows that you have taken clear steps in order to provide suitable protection of personal information. This kind of commitment can, for example, have a positive effect on your competitive position. And while many organizations claim that they take data protection seriously, you have proven that you actually do so.
In addition, implementation of ISO 27701 provides you with insight and control when it comes to privacy. This means that you retain control of how personal data is handled in your organization.
Implementation of ISO 27701 can show customers, partners and other stakeholders that your organisation takes privacy very seriously and is truly committed to personal data protection. This means that you gain a good reputation which is based on transparency.
A certified PIMS means that you can show different interest groups, and in particular your customers, that you take data protection and privacy obligations seriously and take appropriate security measures. And as PIMS also insists on control of the rest of the processing chain, your customers will develop even greater trust in you.
When you start with ISO 27701, you are working systematically to achieve privacy protection whose structure is examined during the certification process. This alone offers you a good overview of your current status as regards privacy and of how legislation affects you during Compliance projects.
This evidence makes internal monitoring by your own data protection officers very efficient. And you are also in a position to provide suitable evidence of personal privacy in the case of external checks or audits by a public authority.
We find increasingly that organizations which are assessed in the course of supplier management have to do less work for the assessment if they hold certification. For example, some customers accept ISO 27001 certification instead of the data security part of the audit, and ISO 27701 certification instead of the privacy part. Therefore organizations no longer have to appoint an independent external auditor to demonstrate compliance.
Both certifications together can fulfil the requirements of your customers.
If you can demonstrate that you are committed to personal privacy, you can also be secure in your knowledge of the subject. Anxiety regarding data protection and privacy has increased considerably in recent years, and certification to ISO 27701 can play a major role in assuring the public of your commitment and competence.
Your reputation as an organization which really does take privacy seriously strengthens your position on the market. ISO 27701 certification is an additional advantage which means that you can give a guarantee to your customers that by practising data security, you are working systematically to protect personal data.
Content of ISO 27701
ISO 27001 and ISO 27002 contain requirements and guidelines for an Information Security Management System (ISMS). ISO 27701 adds requirements and guidelines specific to privacy and expands them into a Private Information Management System (PIMS).
ISO 27701 acts as an extension of the requirements and controls of ISO 27001 and the implementation guidelines of ISO 27002 and does not function as a stand-alone. Therefore it necessarily has the same or a smaller scope as the ISO 27001 management system on which it is based.
The first substantive part of PIMS is chapter 5 and connects privacy (ISO 27701) to information security (ISO 27001) be means of specific privacy requirements on top of the requirements of the (already existing) information security management system. These additional PIMS-specific requirements are limited to chapters 4 (Context of the organization) and 6 (Planning). For example, the people whom the personally identifiable information (PII) relates, the so called PII principals, must now also be included in the interested parties along with their needs and expectations. More important the risk management approach must now also include the potential impact on the privacy of these principals. In order to mitigate the risks, which are now information security as well as privacy risks, the organization now has to take the additional privacy controls into consideration that are set out in the appendices. Appendix A for controllers and appendix B for processors. Represented in a statement of applicability (SOA) in the same way the organization is familiar with in the (existing) ISMS.
Chapter 6 is dedicated to giving additional privacy specific guidance on top of the implementation guidelines in ISO 27002. Helping the organization by integrating privacy into the (already existing) information security controls. For example in appointing an independent privacy expert as part of the implementation of the organizations roles and responsibilities.
The chapters 7 and 8 act as implementation guidelines for the controls in the appendices A and B of ISO 27701. The equivalent of ISO 27002 towards Appendix of ISO 27001. There is no ISO 27702. It is all covered in ISO 27701.
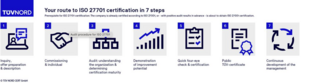
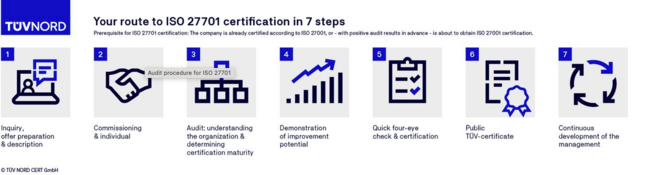
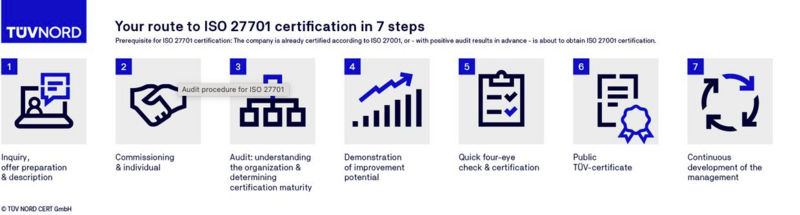
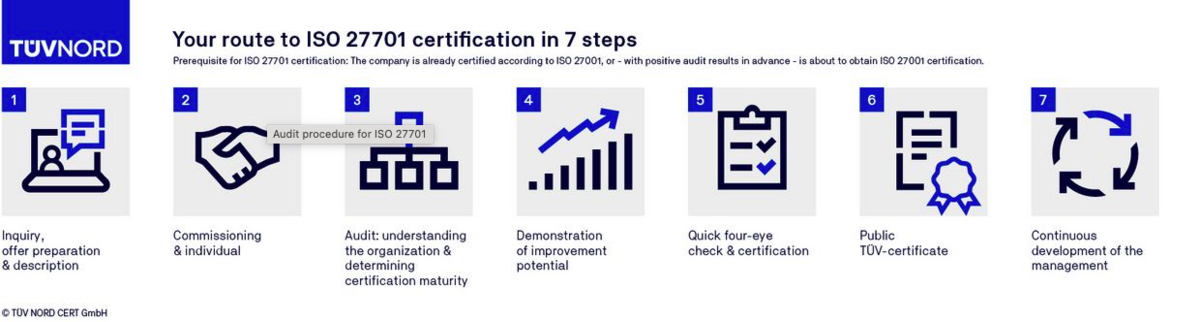
FAQs on ISO 27701
An ISO 27701 certificate is suitable for every organization which processes personally identifiable information (PII), regardless of size. It applies for public and private organizations, governmental authorities and charitable bodies which process PII within the framework of an ISMS as Controller or Processor.
Above all if you have to demonstrate that your organization has a deliberate policy with regard to this type of personal data, the certificate offers a structured solution:
- Every organization that processes personal data, regardless of its size and type, can benefit from the introduction of ISO 27701.
- Organizations wishing to alleviate the financial and regulatory risks involved in privacy breaches
- Private, public and even governmental authorities which have to follow a risk-based approach to the storage and processing of personal data
Organizations with an ISMS who wish to further develop their role as Controller and/or processor and increase their professionalism
Organizations that are subject to Indonesian law, e.g. because they are Indonesian or are active in the Indonesia, can make use of ISO 27701 in order to examine their observance of the PDP Law more closely. This applies to the following, for example:
- Organizations who seek a way of fulfilling the requirement that they have used suitable and technical and organizational means in order to ensure observance of the requirements of the PDP Law.
- Organizations wishing to (further) process personal identifiable data on behalf of customers who by law are only permitted to subcontract to organizations which can sufficiently demonstrate that the processing fulfils the requirements of the PDP Law and protects the rights of those affected.
In order to achieve ISO 27701 certification you must already operate a functioning ISMS which fulfils the requirements of ISO 27001. This means that you already have certification to ISO 27001 or are in the process of gaining it. The reason is that ISO 27701 is an extension to and augments ISO 27001.
This additional standard is certainly relevant for every organization which works with sensitive personal information.
If you already hold an ISO 27001 certificate (through TÜV NORD or another certification body), you will first be subject to a separate audit for ISO 27701. The ISO 27701 certificate will have the same term of validity as your current ISO 27001 certificate. When this expires, or if you begin with ISO 27001 and ISO 27701 at the same time, the audits for ISO 27001 and ISO 27701 are synchronised.
The ISMS and the PIMS are then integrated and the audits for both systems can be combined.
TÜV NORD Preliminary Tools on Self Assessment Checklist for ISO/IEC 27701
Please contact us
Arkadia Green Park, Tower F 6th Floor, Suite 602-604, Jl. TB. Simatupang Kav.88, Kebagusan, Pasar Minggu, 12520 Jakarta Selatan.